Cyber security isn’t just about firewalls and antivirus software anymore. As technology evolves, so do the tactics of cybercriminals. Whether online or offline, there are numerous ways your data and privacy can be compromised—often in ways most people don’t think about. Here are six cyber security practices that might not be on your radar—but should be.
1. Avoid Unknown Wi-Fi Networks
Wi-Fi is incredibly convenient, but connecting to the wrong network can be a serious security risk. Hackers can set up fake hotspots that mimic legitimate public networks, like naming one “FlyAirport” near an airport lounge. Once you connect, they may intercept your data or capture login credentials.

If you ever need to access the internet in public, consider using a personal hotspot or a trusted VPN instead. Implementing a VPN is as simple as calling your Managed IT Provider today, and can be the key tool to stopping a public wi-fi breech.
2. Always Lock Your Laptop—Even for a Quick Break
Cybersecurity isn’t just about online threats. Unattended devices pose a real risk in shared or public spaces. Sensitive information on your screen can be viewed or stolen in seconds. Even well-meaning coworkers or clients might accidentally see something they shouldn’t. Always lock your device when stepping away. In addition, ask your Managed IT Provider to verify your system settings hide notifications while your laptop is locked.
Quick Tip: Use Windows + L (or Control + Command + Q on Mac) to instantly lock your screen.
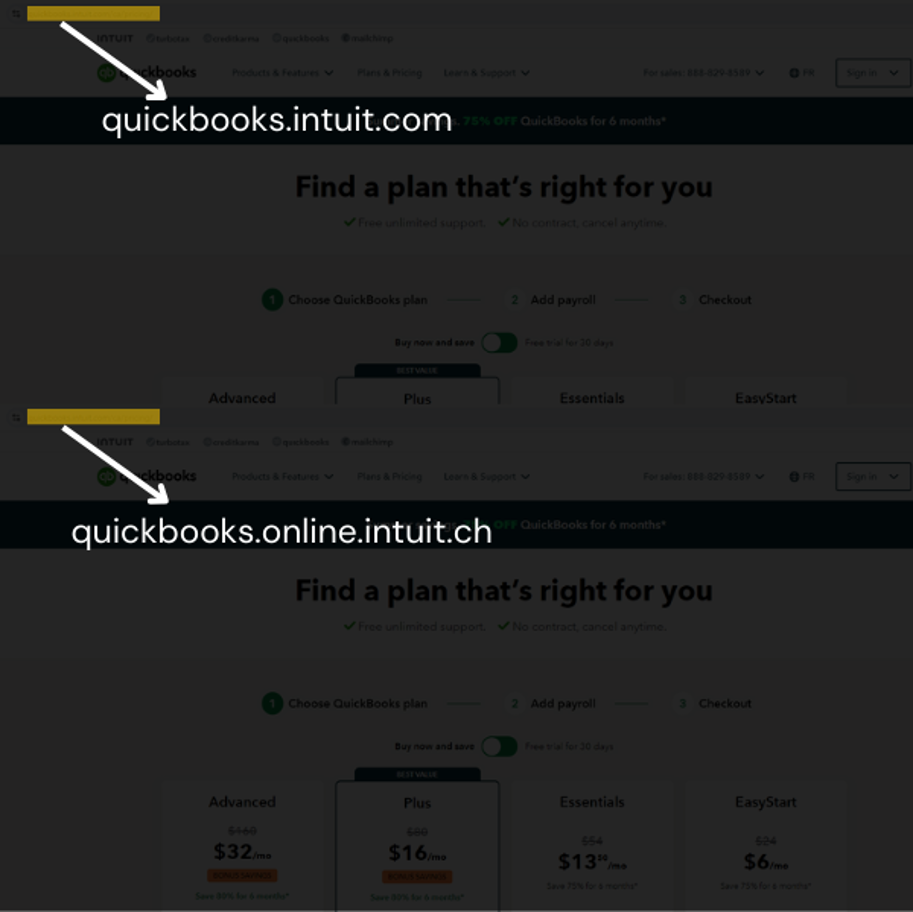
3. Double-Check URLs for Spoofing
Some fake websites are obviously sketchy, but others are nearly indistinguishable from the real thing. “Script spoofing” is a tactic where cybercriminals clone a legitimate site and change the URL ever so slightly—like switching .ca to .ch, or replacing an “l” with a capital “I”.
Before entering any sensitive information, carefully inspect the website address. If something feels off, trust your instincts and verify. If you do end up accidentally clicking on a scamming website, don’t panic. Send a quick email to your Managed IT Provider and check to make sure your device is still fully secure.
4. Verify, Don’t Assume—Even in Person
Social engineering isn’t limited to emails or phone calls. Sometimes it’s someone in a hard hat with a clipboard claiming to check your building’s security system. If you’re unsure about someone’s identity or reason for being on-site, don’t be afraid to ask for credentials or check with management. A legitimate visitor will appreciate your diligence because it helps protect everyone. If someone ever calls or visits and claims to be your IT Provider, make sure they are a trusted individual before you let them access your device.

Techdoz always introduces new technicians before allowing them to come onsite alone. We’re one call away from verification if you ever are unsure!
5. Treat Public AI Tools Like Public Forums
Generative AI tools are powerful and incredibly helpful, but they’re not private. Anything you input into a public AI platform may be stored or used to train future models, meaning it could potentially be seen or inferred by others. Never share confidential information with AI tools unless your organization has vetted them for secure use. A good rule of thumb: If you wouldn’t want a competitor to see it, don’t paste it into AI.
6. Clear Your Cookies Regularly
You’ve likely seen cookie consent banners on nearly every site you visit. These cookies track your behavior, preferences, and sometimes personal data. While they’re often used for harmless purposes like personalized ads, they can also be used to build detailed profiles or even be sold to third parties. Make a habit of clearing your cookies and using privacy settings in your browser to limit data tracking.
Final Thoughts
Cyber security isn’t just your IT Provider’s job – it’s a shared responsibility. By staying informed and adopting smart habits, you can help protect your personal data and your organization’s information from unexpected threats. Sometimes, the most effective defenses come from the quickest daily precautions.
If you found this article helpful, click here for more information about our cyber security training. We provide comprehensive cyber security courses built to empower your employees against cyber threats.
